
In June 2025 I presented a talk at Identiverse 2025 about decentralized identity called I’m Just George – Living in a Decentralized Identity World. Today I presented a slightly updated version of this talk to an internal audience at McDonald’s as part of our Tech Talks series. The title and pop culture references were inspired by the song “I’m Just Ken” from the Barbie movie, which my daughter was playing essentially on repeat when I started thinking about this topic.
As the world of digital identity continues to rapidly evolve, one of the developments I’m most interested in is the concept of decentralized identity and verifiable credentials. While standards and implementations are still early, decentralized identity systems promise enhanced security, privacy, and user control. In this post we’ll explore what decentralized identity is, why it matters, and how it’s helping shape the future of authentication, trust, and digital credentials.
What is Enterprise Identity like today?
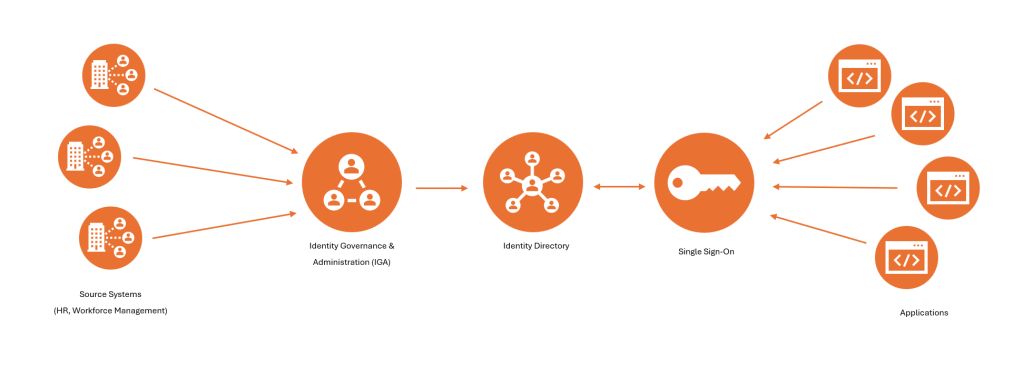
Traditional enterprise workforce identity systems are typically centralized systems that utilize source systems like HR and workforce management to drive user identity lifecycle events. These identities are governed by Identity Governance & Administration (IGA), stored in directories, and used to access applications via single sign-on.
All user information needed as part of the identity and access management (IAM) processes needs to be stored and moved around these central systems, often leading to security and privacy concerns.
What Is Decentralized Identity?
Decentralized identity is a system where individuals control their personal information without relying on a central authority. Using distributed ledger technologies, users can create and manage digital identities securely and privately. Key features include:
- Enhanced Security & User Privacy: Individuals manage and control how their identity data is shared and used. Strong cryptography reduces the risk of data breaches and unauthorized access.
- Verifiable Credentials: Digital certificates stored in a user’s identity wallet are issued and signed by trusted entities. These credentials prove specific things about the user like their age or education.
- Distributed and Secure: Decentralized identity uses distributed technologies such as blockchain and distributed ledgers to ensure privacy, security, and tamper-proof credentials.
- Interoperable: Interoperability protocols are being developed by standards bodies to ensure decentralized identity can work seamlessly across different platforms.
Ken is me.
—barbie (2023)
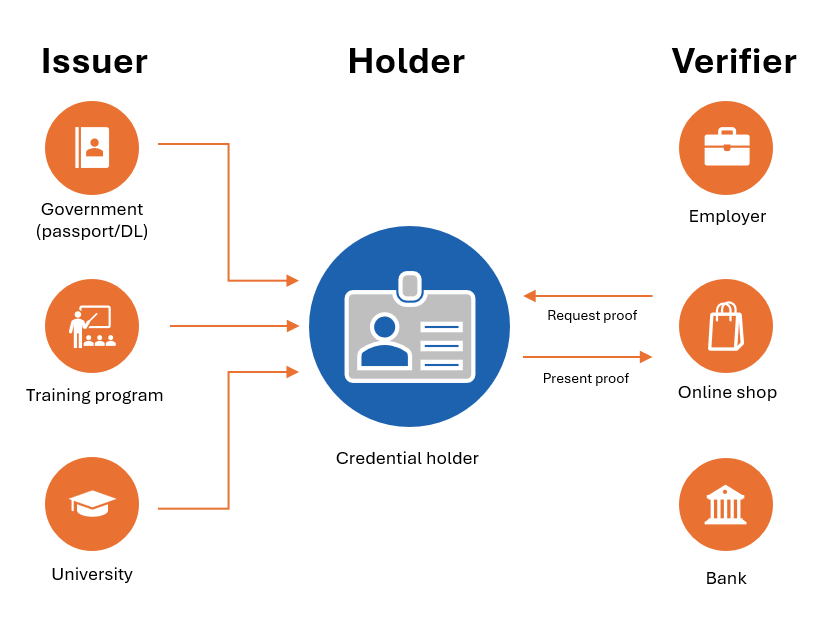
In this model, Issuers (e.g., governments, universities, banks) provide credentials, Holders (users) store them, and Verifiers (employers, online shops) request proof.

- Issuers: Issue credentials to users (the Holder) and verify the credential when requested by the Verifier.
- Holders: Owners of verifiable credentials (the users). The Holder receives the credential from an Issuer and stores it in their identity wallet. They present the credential when prompted by a Verifier.
- Verifiers: A Verifier (for instance, an employer) requests credentials from Holders and verifies them with the Issuer for authenticity and validity.
The simulation is real enough to fool anyone.
—ready player one (2018)
There are several emerging threats that decentralized identity and verifiable credentials can help mitigate:
- Deepfakes in Hiring: Fraudulent job candidates use deepfakes for scams and cyberattacks.
- Executive Impersonation & Financial Fraud: Attackers create fake videos or audio to trick employees into transferring funds or sharing sensitive data.
- Phishing & Social Engineering: Deepfake-enhanced emails and calls increase the risk of credential theft.
- Disinformation & Reputational Damage: Fabricated media can harm brands and public trust.
- Bypassing Biometric Security: Deepfakes can spoof facial recognition, granting unauthorized access.
It’s not what you know, it’s what you can prove.
—Training day (2001)
Decentralized identities and verifiable credentials help address these challenges:
- Immutable Verification: Decentralized identity creates tamper-proof records of identity credentials that can be cryptographically verified, making it harder for bad actors to impersonate someone using deepfake videos or audio.
- Eliminating Central Points of Failure: With decentralized identity, identity data is stored across a network, reducing the risk of a single point of failure that deepfake creators could exploit.
- Selective Disclosure & Zero-Knowledge Proofs: Users can verify their identity without exposing unnecessary personal information. This prevents attackers from obtaining details that could be used to create more convincing deepfakes.
- Credentialed Authenticity for Content Creators: Journalists, influencers, and public figures can digitally sign their content using decentralized identity, proving that videos or statements genuinely come from them. This can help counter misinformation spread through manipulated media.
- Automated Fact-Checking & Authentication: AI-driven tools can cross-check a person’s decentralized identity with their digital presence, flagging potential deepfake content in real time before it spreads widely.
You don’t need to see his identification.
—star wars: episode IV – a new hope (1977)
How can enterprises benefit from decentralized identities in the future?
- Employee Credentials: Enhance hiring processes by verifying new hires quickly by checking digital degrees, certificates, or background checks.
- Training and Compliance: Employee internal training certifications can generate digital credentials that can be verified by internal process and access systems.
- Partner & Supplier Trust: Third party suppliers and vendors can share compliance documents as Verified Credentials without exposing underlying data.
- Digital Onboarding: Streamline onboarding and continuously verify external workers.
- Cross-Company Credentials: Enterprise ecosystems can issue membership or accreditation Verified Credentials (e.g., certified partner of a company) which can be validated via shared registries or trust networks.
We must think not as individuals but as a species.
—interstellar (2014)
One of the challenges with decentralized identity and verified credentials is that they typically require the user to have a smart phone and use an identity wallet to store credentials. While smartphones are becoming more widely used, not everyone has one. Additionally, in enterprise scenarios, not all users will be issued work smartphones and the user of personal devices for work activities cannot typically be mandated.
As an industry we need to think about how to support these users. Here are some suggested alternatives, though they may not work for all situations:
- Physical Identity Cards with Cryptographic Features: Organizations can issue printed credentials embedded with QR codes or NFC chips that securely store identity data, allowing users to verify themselves at kiosks or service points.
- Secure Paper-Based Alternatives: Verified credentials can be printed as tamper-proof certificates that users carry and present when needed. These can be scanned and verified against decentralized registries.
- SMS & USSD-Based Solutions: For users with basic mobile phones, enterprises can provide identity verification through SMS-based authentication or USSD codes, ensuring accessibility without requiring smartphone apps.
- Shared/Public Kiosk Access: Identity terminals in banks, retail locations, or government offices can help users access their credentials securely without requiring personal devices.
- Assisted Credential Management: Enterprises can set up support centers where personnel assist users in retrieving or presenting credentials on their behalf, ensuring inclusivity while maintaining security.
- Identity Custodianship: Trusted agents or institutions (like banks, local government offices, or nonprofits) can act as custodians of decentralized identities, enabling users to authenticate securely without personal digital devices.
Leeloo Dallas, multipass.
—The Fifth Element (1997)

Key standards driving decentralized identity:
- W3C Verifiable Credentials 2.0
- W3C Decentralized Identifiers
- ISO/IEC 18013-5/18013-7 – Mobile Driving License (mDL)
- eIDAS 2.0 & European Digital Identity Wallet (EUDI)
Even if you can’t make it perfect, you can make it better.
—Barbie (2023)

Expect innovations that bridge decentralized identity, verifiable credentials, and mobile digital wallets into a single, trusted identity framework.
Over the next few years, a significant focus will be on bridging decentralized identity standards like W3C Verifiable Credentials (VCs), eIDAS 2.0, and mobile driver’s licenses (mDLs) to create comprehensive digital identity ecosystems within standard digital wallets. Several trends point to this convergence:
- Collaboration between regulatory bodies and tech developers
- Standardized verification frameworks
- Global adoption of digital wallets: Governments and enterprises are deploying identity wallets for citizens and employees, making interoperability between standards essential.
- Regulatory push (eIDAS 2.0 & global initiatives): The EU’s EUDI Wallet will incorporate Verifiable Credentials, setting a precedent for other regions to follow. The U.S. and various governments are exploring mDLs that align with decentralized identity principles.
- Convergence of centralized and decentralized approaches: eIDAS 2.0 enforces a trusted, regulated identity framework, while W3C VCs enable self-sovereign, user-controlled identity. The challenge ahead will be harmonizing these models to balance trust, compliance, and user autonomy.
- Cross-platform identity verification: Enterprises and governments will prioritize interoperability, ensuring that credentials work across different wallets, regions, and applications.
- Authentication beyond borders: Users will demand global trust frameworks allowing mobile driver’s licenses, passports, and financial credentials to work seamlessly across different ecosystems.
To make this future a reality, there needs to be:
- Collaboration between regulatory bodies and tech developers (governments, OpenID Foundation, W3C, Hyperledger).
- Standardized verification frameworks that allow users to present credentials without vendor lock-in.
- Improved wallet security to prevent fraud and unauthorized credential use.
Be prepared.
—The Lion King (1994)
Technology leaders must prepare for transformations driven by:
Decentralized identity will transform how users control and share personal data. While mainstream adoption may take time, progress is accelerating, especially in financial services and healthcare.
Consumers, employees, and partners are increasingly demanding that enterprises and other entities protect their data and their privacy. Governments are stepping in with regulations to ensure this. Deepfakes and AI are pushing us toward a zero-trust world where verification is essential.
The world is changing. Decentralized identity may not impact you immediately, but it’s coming. Start asking questions, reading, and learning to stay ahead of the curve.
The world is changing. Can you feel it?
—The Lord of the Rings: The Two Towers (2002)
Further Reading
- Beginner’s Decentralized Identity Guide for 2025
- What Is Decentralized Identity? The Ultimate Beginner’s Guide
- Verifiable Credentials 2.0: What the W3C’s 2025 Standards Mean for Digital Certification
- The Application of W3C Verifiable Credentials in Modern Digital Scenarios: A Comprehensive Guide
- The EU Digital Identity Wallet: What You Need to Know
You must be logged in to post a comment.